#OpSaveGaza Persists Against Israeli Websites

As previously reported by SITE Intelligence Group, the Anon Ghost Team hacking group announced on July 3 the creation of Operation Save Gaza, a campaign scheduled to take place on July 11 against Israeli websites in response to recent violence in Gaza. The campaign was widely accepted by various hacking groups and developed into a massive cyber-attack, with over 2000 websites being affected.
Although Anon Ghost Team has been responsible for most hacks in the campaign, many hacking groups and individuals have joined Anon Ghost Team in attacking Israeli domains using Distributed Denial of Service (DDoS) attacks, website defacements, and database hacks and leaks. Among the groups that participated in the cyber attacks were the Anonymous collective, Izzah Hackers, Tunisian Hackers Team, the Indonesian Cyber Army, the Middle East Cyber Army, the Muslim Liberation Army, and Anonymous Arab.
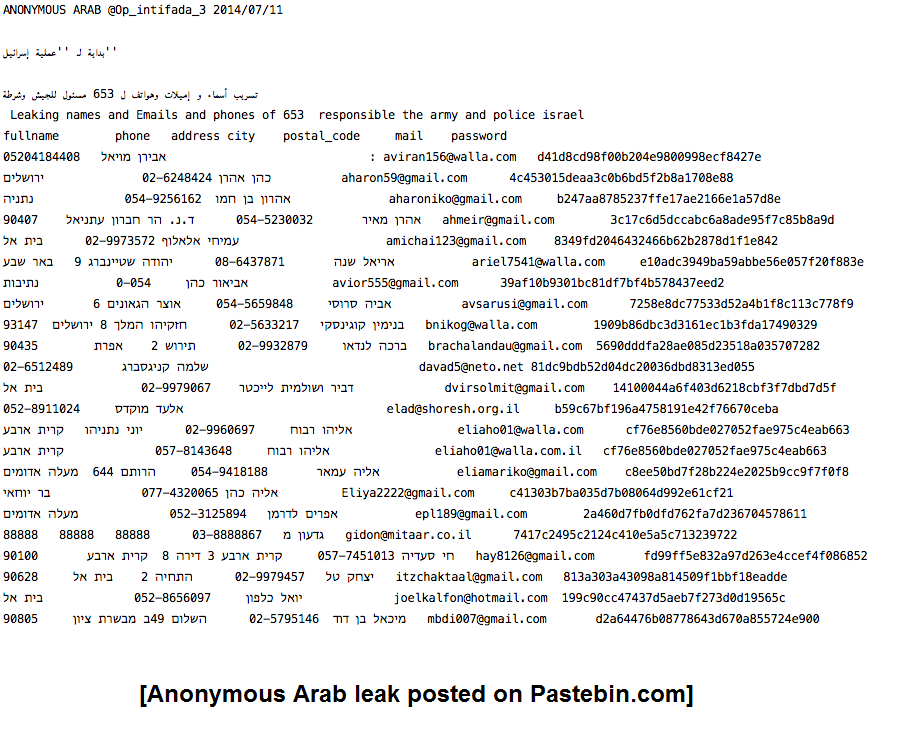
Anonymous Arab, one of the groups that participated in Operation Save Gaza, posted messages illustrating that it purportedly stole contact information of 653 Israeli military and police officials. On July 11, the group published a Pastebin.com page that provided names, email addresses, phone numbers, and encrypted passwords. It contained the message:
Beginning of “Israel Operation”
Leaking names, emails, and phone numbers for 653 officials of the Army and Police.
Throughout July 11, more groups began joining in the attacks and posting their accomplishments to Twitter.
Noting Operation Save Gaza’s political focus, tt is not surprising that many of the data leaks, DDoS, and defacements—which constituted the overwhelming majority of the attacks—targeted websites of government agencies, including the Israeli Air Force, the Israel Ministry of Foreign Affairs, the Israeli Defense Forces, the Israeli Parliament, the Israeli President, and Mossad. Similarly, companies that work with the government and military were also attacked, including Defensoft.
Among the non-governmental companies the hackers claimed to have breached were the Israel Bank, Jewish Life TV, and the Dead Sea Regional Enterprises Company.
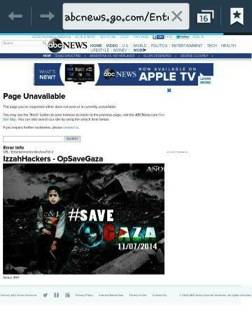
Interestingly, Israeli agencies were not the only ones affected. A group called Izzah Hackers claimed to have defaced the website for ABC News in retaliation for misrepresentation of footage by one of the channel’s anchors, Diane Sawyer, who purportedly confused footage of Palestinians in the wake of an Israeli air strike for Israelis following a rocket attack, tweeting:
@ABC News XSS ‘defaced’ for being Zionist mouthpiece for Israel.
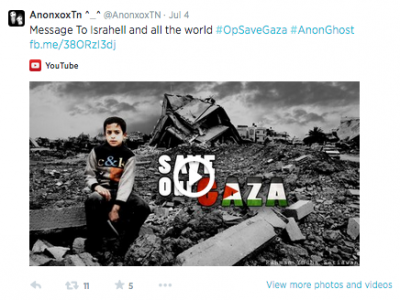
During the campaign, the Twitter hashtag “#OpSaveGaza” became popular with other supporters of Gaza—not just the hacking community. The hashtag was created on July 4 in a Twitter message that reads:
Message to Israhell and all the world #OpSaveGaza #AnonGhost fb.me/38ORzl3dj” and contains a link to the video announcing Operation Save Gaza.
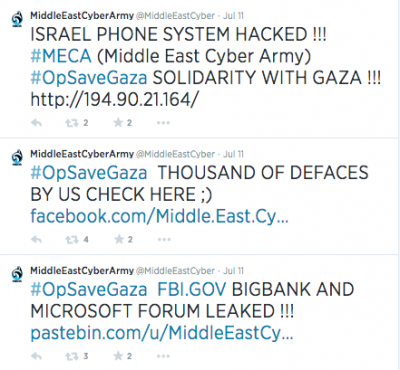
Since its creation approximately 20 days ago, the hashtag has been used 38 thousand times. Indeed, many of the participants in the campaign tweeted their successes using the hashtag. On July 11, the Middle East Cyber Army posted several messages on Twitter claiming to have defaced a thousand of websites and hacked several others, including the Israel phone system, the Federal Beraeu of Investigations, “BIGBANK,” and the Microsoft Official Forum database, although only the link for the Microsoft database can still be found on the group’s Pastebin.com account.
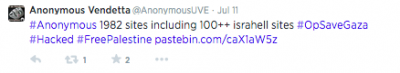
Anonymous Vendetta claimed that nearly 2000 websites were defaced, over 100 of which were Israeli, and provided links to the mirrors of the defacements.
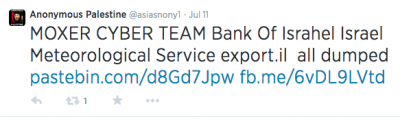
Also on July 11, Anonymous Palestine tweeted: “MOXER CYBER TEAM Bank Of Israehel Israel Meteorological Service export.il all dumped.” The tweet also contained a link to a Pastebin.com page which allegedly contained leaked data of the Israel Export & International Cooperation Institute, the Israel Meteorological Service, and the Bank of Israel.
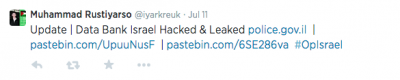
On the same date, the Twitter account of Muhammad Rustiyarso posted two links to Pastebin.com pages, writing:
Update | Data Bank Israel Hacked & Leaked police.gov.il | pastebin.com/UpuuNusF | pastebin.com/6SE286va #OpIsrael.
The first linked Pastebin.com contained names, email addresses, passwords, and telephone and fax numbers of 21 alleged employees of the Bank of Israel leaked by GhostSec-Team. The second Pastebin.com page asserts that John Milk and the Moxer Cyber Team hacked the website for the Israeli Police and published 24 email and passwords allegedly related to the agency.
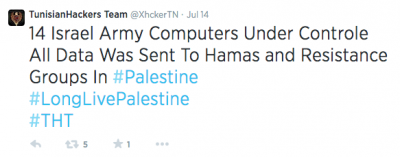
Illustrating the massive tweets of members reporting their successful hacking, Twitter user “TunisianHackers Team” posted a message claiming to have taken control of 14 Israeli Army computers and that the data acquired was sent to Hamas “and Resistance Groups in #Palestine.”
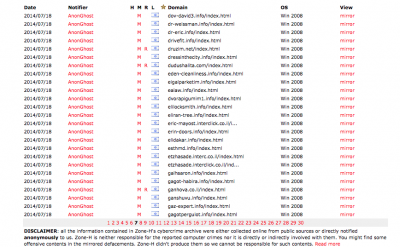
This collective effort seems to have led to a large list of affected sites, most of which suffering defacements, a less-sophisticated form of hacking than DDoS or data leaks. Upon a successful defacement, hackers post the image, along with a mirror, on a website designed to store such mirrors, creating a large database of attacks.
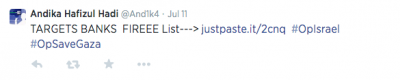
In an effort to cause a large-scale disruption during the operation, some Twitter users tweeted and published information necessary to create an organized DDoS attack. On July 11, user “Andika Hafizul Hadi” tweeted a message stating “TARGETS BANKS FIREEEE List” which contained a link to a pasting site that listed 17 banks to be targeted. Among the banks listed were Bank Hapoalim, Bank Jerusalem, all four subsidiaries of the First International Bank of Israel, Bank Massad, Bank Otsar ha-Hayal, U-Bank, and Poaley Agudat Israel Bank. The document provides the Internet Protocol (IP address), Port and WebHive details of these websites, the information necessary to conduct a DDoS attack.
Responding to this campaign, an alleged Israeli hacking group called Israeli Elite Force (IEF) began a counter-strike entitled “Operation Israel Retaliate” against Palestinian websites and pro-Palestinian groups. Some of the websites attacked included the Palestinian Ministry of Health, the Voice-over-Internet Protocol of Hamas, Iran’s University of Guilan, and the Qatar National Convention Centre. In defense of its attacks, the group cited a speech by Israeli Prime Minister Benjamin Netanyahu in which he asserts if the United States were experiencing the same situation, it too would be forced to respond. The group also stated that there is no solution to this conflict:
Can you give us any solution?
I don’t think so, and why? Because of one reason:
We’re using missile defense to protect our civilians, and they’re using their civilians to protect their missiles. They murderer their own children.
So please, if you think that you hack some low security websites here in Israel and someone really take care of it, you wrong.
We have other things with higher priority to take care of.
But when you all "hackers" publish personal information of Israelis we have to give you back fire.
So sit back, relax and enjoy.
No one will stop us from live in our country!
Long Live Israel!
As can be seen by the persisting attacks and outcries occurring for 20 days, much like in Gaza, the cyber attacks in response to this situation will continue and are unlikely to conclude any time soon.